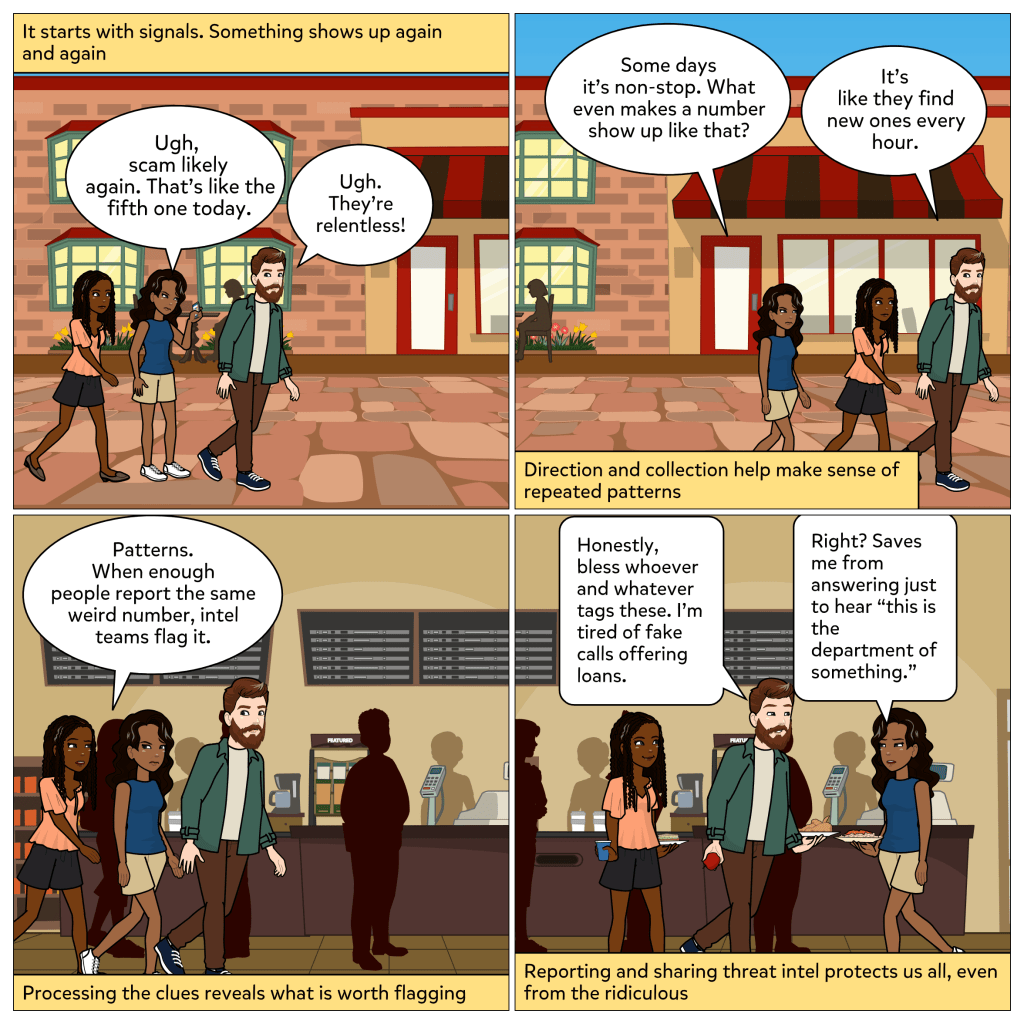
Scam Likely again?
I can already picture the eye roll. You ignore the call. Or maybe you block the number, only to get a similar one just minutes later. Different digits, same feeling. And if you are expecting an important call, nothing feels more annoying than seeing “Scam Likely” pop up instead.
It is frustrating. It is also a signal.
These kinds of alerts: scam calls, sketchy texts, weird links can feel like background noise. But under the hood, they are clues. They are pieces of a bigger puzzle. And learning how to read them is what cyber threat intelligence is all about.
Let’s break it down in plain terms.
Cyber Threat Intelligence (CTI) is not about guessing or gut instinct. It is about collecting real signals, connecting the dots, and deciding what actions to take based on what you learn. From scammy phone calls to phishing emails to data leaks, CTI is the work of turning random noise into meaningful awareness.
And believe it or not, you already use parts of this in your everyday life.
So let’s walk through the Cyber Threat Intelligence Life Cycle using something as simple and annoying as these kinds of scam calls:
1. Direction
This is where you ask the questions. What do I need to know? What are we trying to protect?
For most people, the question sounds like, Why am I getting these calls? Did someone leak my number? It is not about one hacker targeting you. It is about how your info may have landed on a list that is now being recycled and reused.
2. Collection
Now you start gathering data.
You notice that the calls come from similar-looking numbers. Maybe they always happen around the same time. Or they use the same kind of pitch, an unpaid bill, a suspicious login, an urgent tone. These patterns are all part of the signal.
3. Processing
Here is where you sort the real from the noise.
You compare the number to others online. You see if it is part of a known scam. You flag it, report it, and maybe talk to someone else who received the same call. You start to understand the tactic behind the annoyance.
4. Analysis
Now it clicks.
This is not random. It is part of a widespread campaign. Maybe your data showed up in a breach. Maybe it was sold to marketers who did not vet it well. Either way, you realize it is bigger than just your phone.
5. Dissemination
Time to take action and share what you know.
You tell a friend not to answer numbers they do not recognize. You warn your parents. Maybe you even update your phone settings or check your accounts for any related phishing attempts. You spread the word. That is cyber threat intel in motion.
6. Feedback
You reflect and adjust.
You add more filters. You sign up for breach alerts. You start asking, Where else is my info floating around? And just like that, you are more prepared.
This is the power of threat intelligence. It is not reserved for analysts or SOC teams. It is a mindset. One that helps you spot warning signs early and respond with intention.
Because in a connected world, threats will always exist. But so will signals. And knowing how to read them makes all the difference.
What about you?
Have you ever gotten scam calls that made you wonder where your info ended up?
What signals do you tend to overlook?
Let’s keep learning together. Awareness is not about paranoia. It is about being informed. 😊
Leave a comment