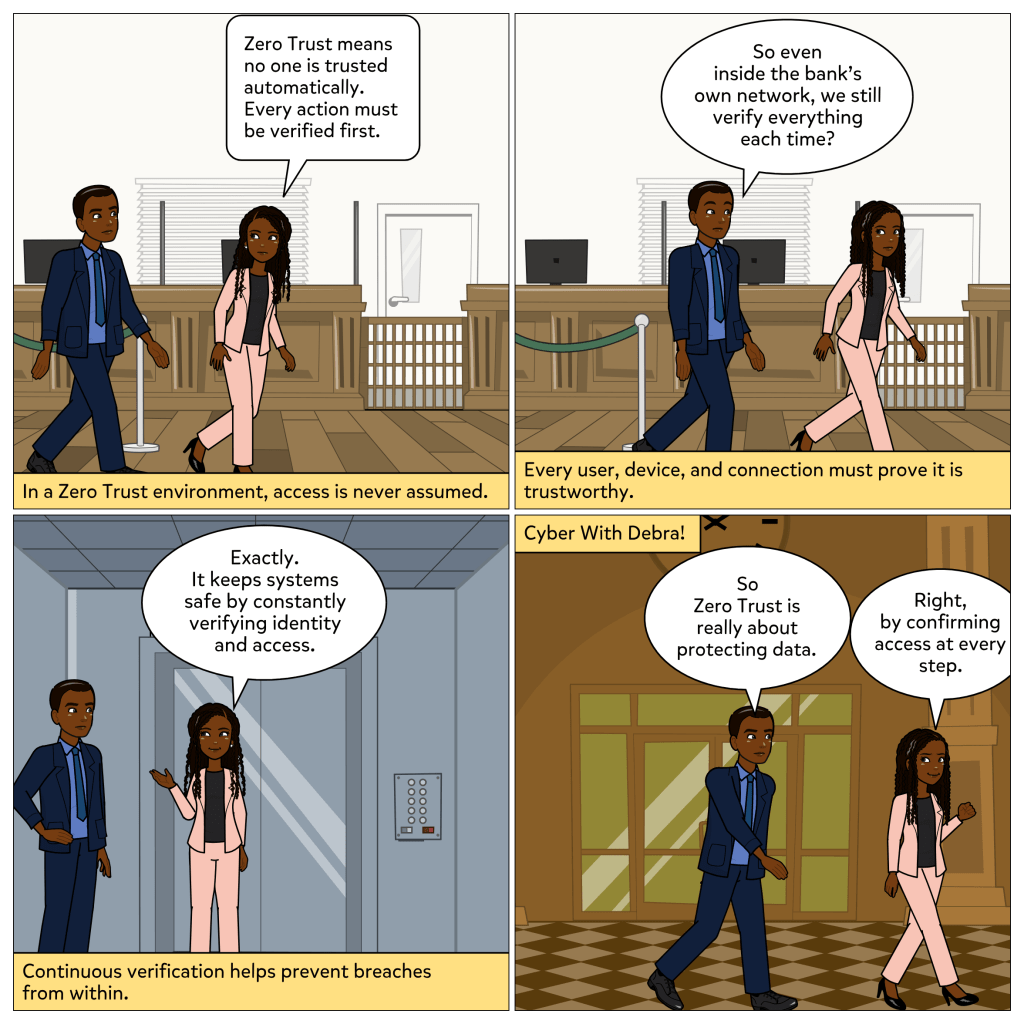
In cybersecurity, trust without verification is a risk few organizations can afford. The idea that everyone inside a network is automatically safe no longer holds up. That is why more industries, including banking, are turning to a Zero Trust approach.
Zero Trust means no one is trusted automatically. Every user, device, and connection must verify who they are before gaining access. It is not about suspicion. It is about assurance.
In this week’s comic, Debra and Ray walk through a bank where security depends on constant verification. Ray is surprised that even employees must reverify to move between areas. Debra explains that this is the point of Zero Trust, protecting data by confirming access at every step.
What Zero Trust really means
Zero Trust is built on a straightforward principle, never trust, always verify. It recognizes that modern threats can come from anywhere, even from inside an organization. The model focuses on controlling access, validating identity, and monitoring activity continuously.
A strong Zero Trust framework often includes:
• Identity verification using methods like multi-factor authentication
• Device validation to confirm systems are updated and secure
• Least privilege access so users only have the permissions they need
• Ongoing monitoring to detect and respond to unusual behavior
Why it matters
In sectors like banking or healthcare, where information is sensitive and regulated, Zero Trust limits the damage one compromised account or device can cause. It replaces broad, open access with a model built on context and verification.
Zero Trust works because it closes gaps quietly and consistently. It is less about walls and more about awareness, knowing who is connected, what they are doing, and why.
Everyday takeaway
Think of it like walking through different parts of a bank. Even as an employee, you cannot enter every area without checking in first. Those extra steps protect the vault, the data, and everyone who depends on them.
Zero Trust brings that same discipline to cybersecurity. It turns verification into protection, one access request at a time.
Thank you for reading. I hope you have subscribed. Let me know in the comments how your view of trust has evolved in the digital age. 🔐
Leave a comment