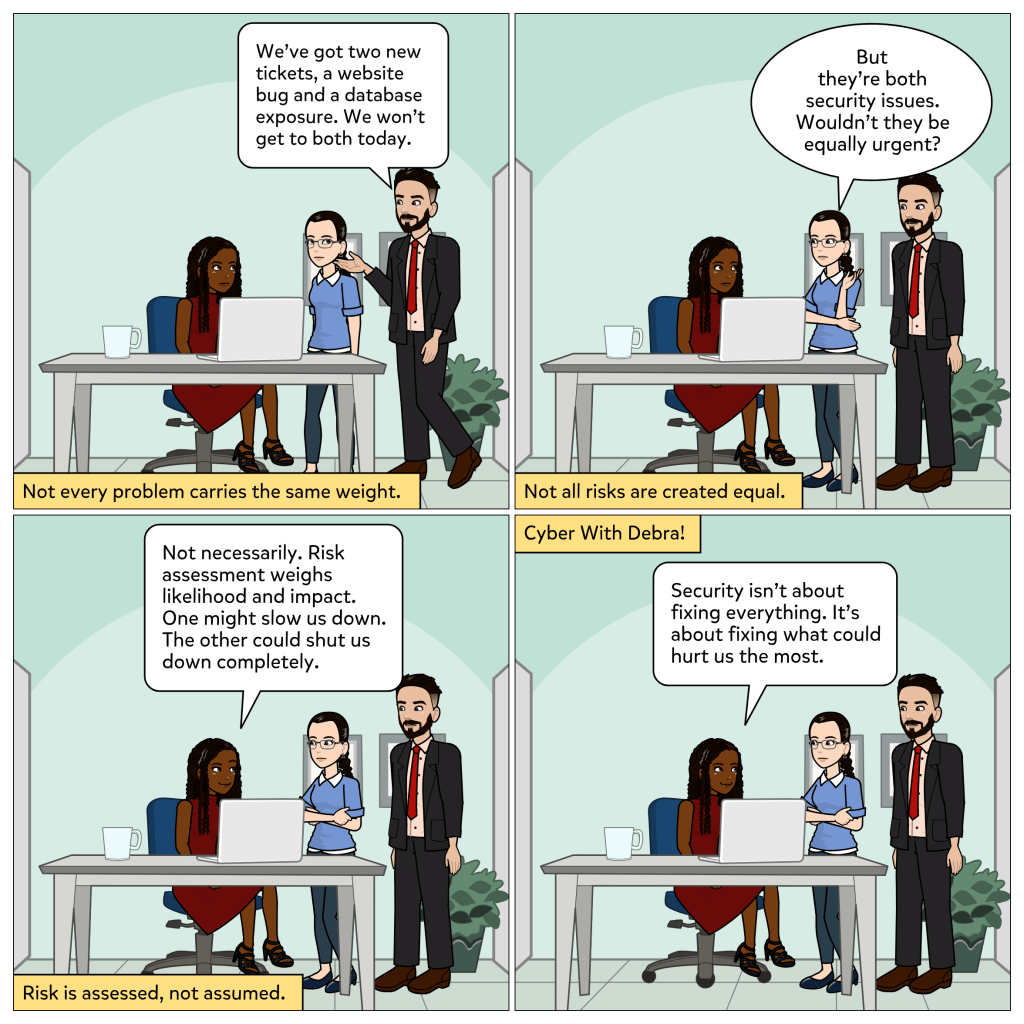
Security issues do not all carry the same weight. Some problems are inconvenient. Others can threaten the entire organization.
In this week’s comic, Joe mentions two new tickets: a website bug and a database exposure. Both are security concerns, but the team cannot address both immediately. Maria wonders if they should be treated as equally urgent.
Debra explains that risk assessment helps organizations decide what to prioritize. It weighs likelihood and impact. One issue might slow operations down. The other could shut them down completely.
Risk is not guessed. It is evaluated.
What risk assessment really does
Risk assessment is the process of identifying potential threats, evaluating how likely they are to occur, and determining the impact they would have if they did.
Organizations use risk assessment to:
• Identify vulnerabilities and threats
• Estimate likelihood of exploitation
• Measure potential impact on operations, data, and reputation
• Prioritize remediation efforts
• Decide whether to mitigate, transfer, accept, or avoid risk
Without assessment, teams may waste time fixing minor issues while serious exposures remain unresolved.
Risk assessment provides structure to decision making.
Why it matters
Security resources are limited. Time, personnel, and budget cannot address everything at once.
If every issue is treated as equally urgent, teams lose focus. Critical risks may not receive the attention they require.
By evaluating both likelihood and impact, organizations can focus on what could cause the most harm. This ensures that security efforts align with business priorities.
Risk assessment turns reaction into strategy.
Everyday takeaway
Not every warning deserves the same response.
In cybersecurity and in daily life, the most effective decisions come from understanding consequences, not just reacting to urgency.
Security is not about fixing everything. It is about fixing what could hurt the most.
Thank you for reading. I hope you are subscribed. What factors do you think organizations should consider most when evaluating risk? ⚖️