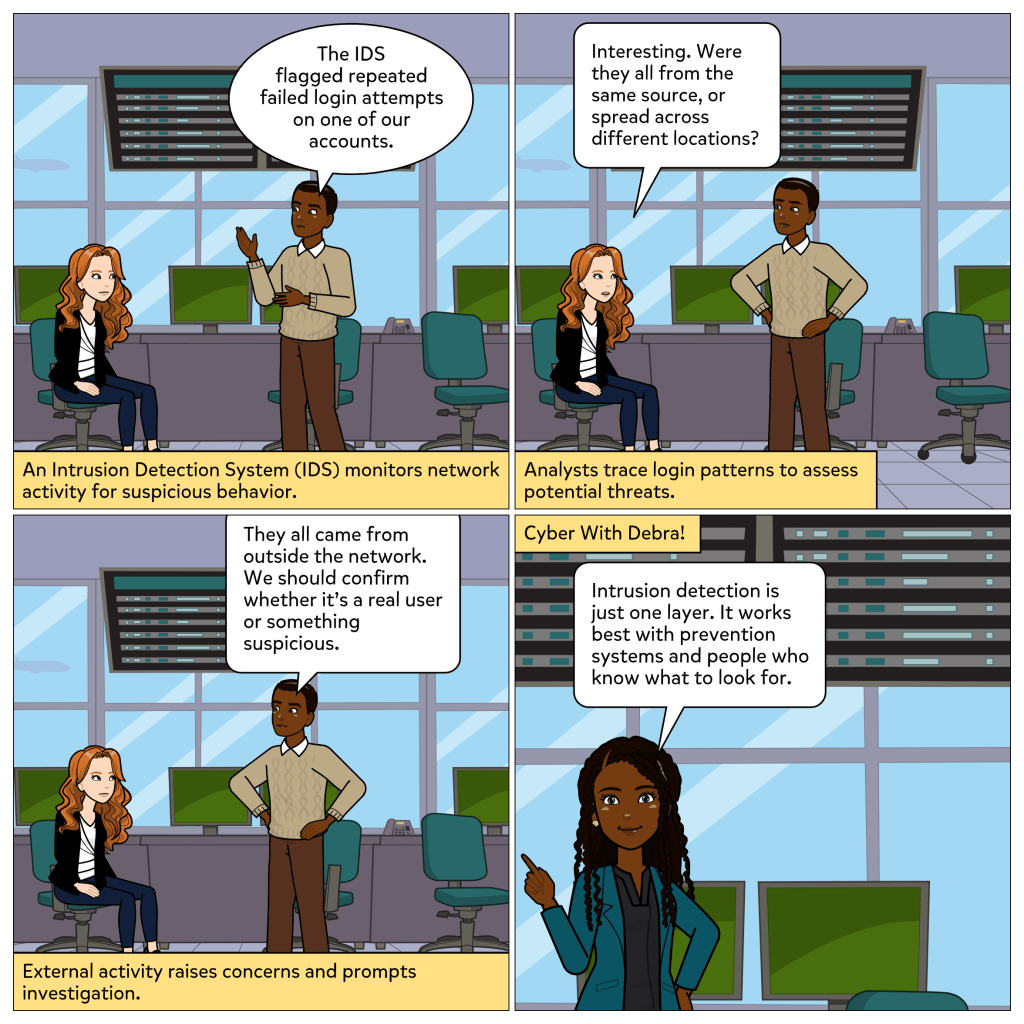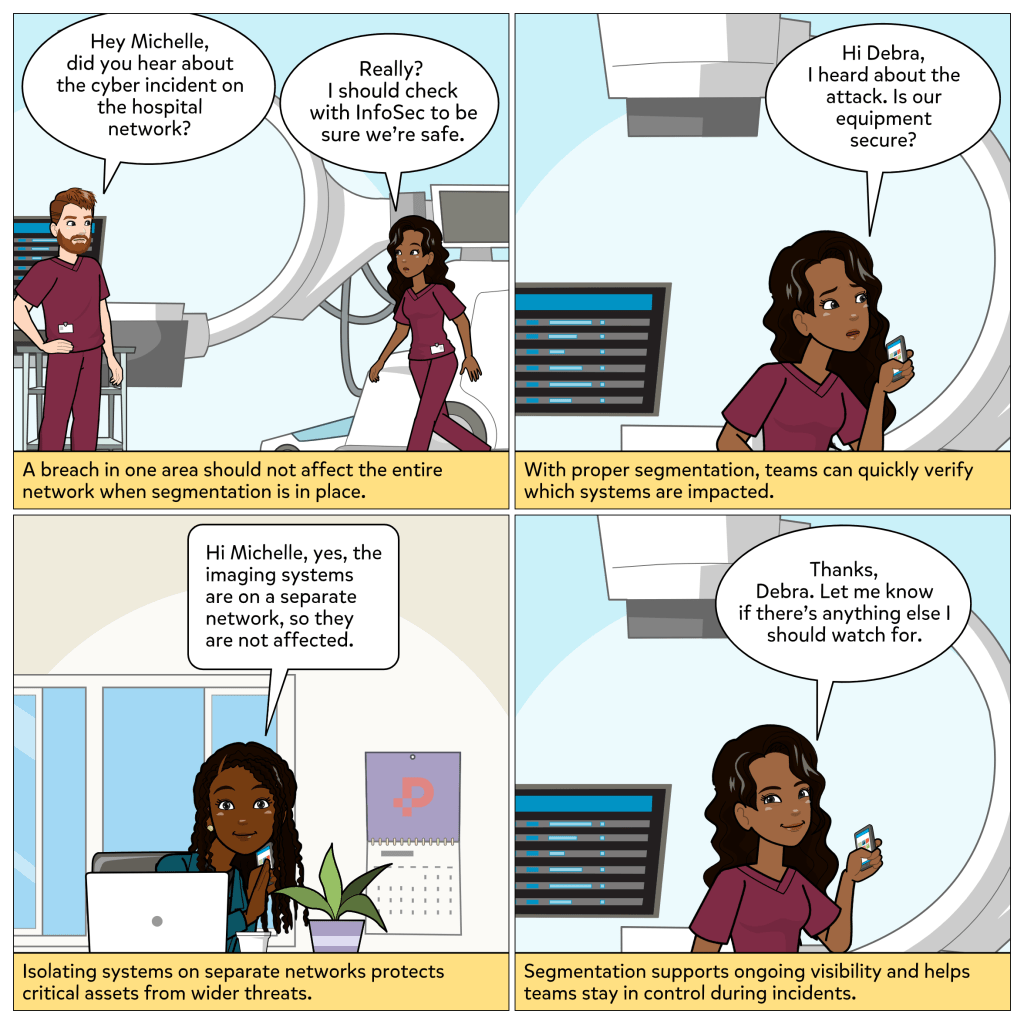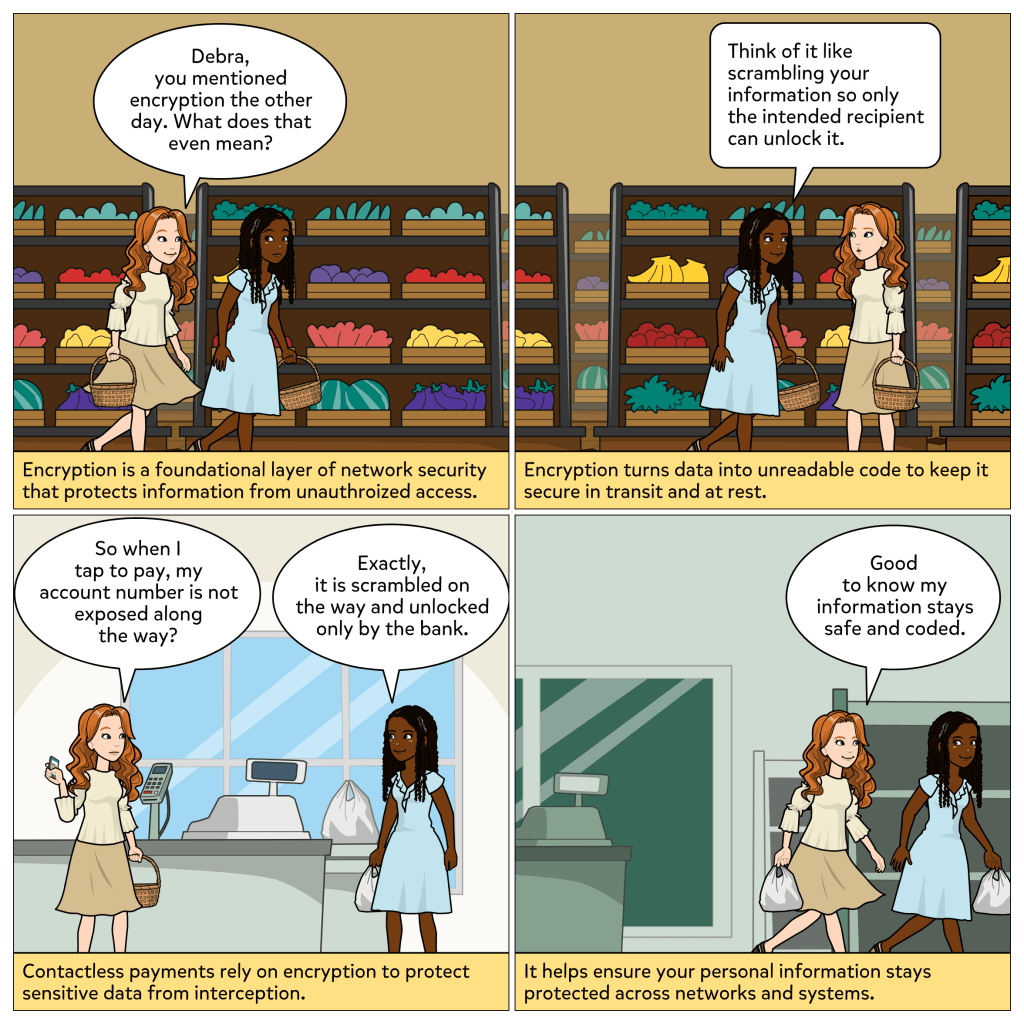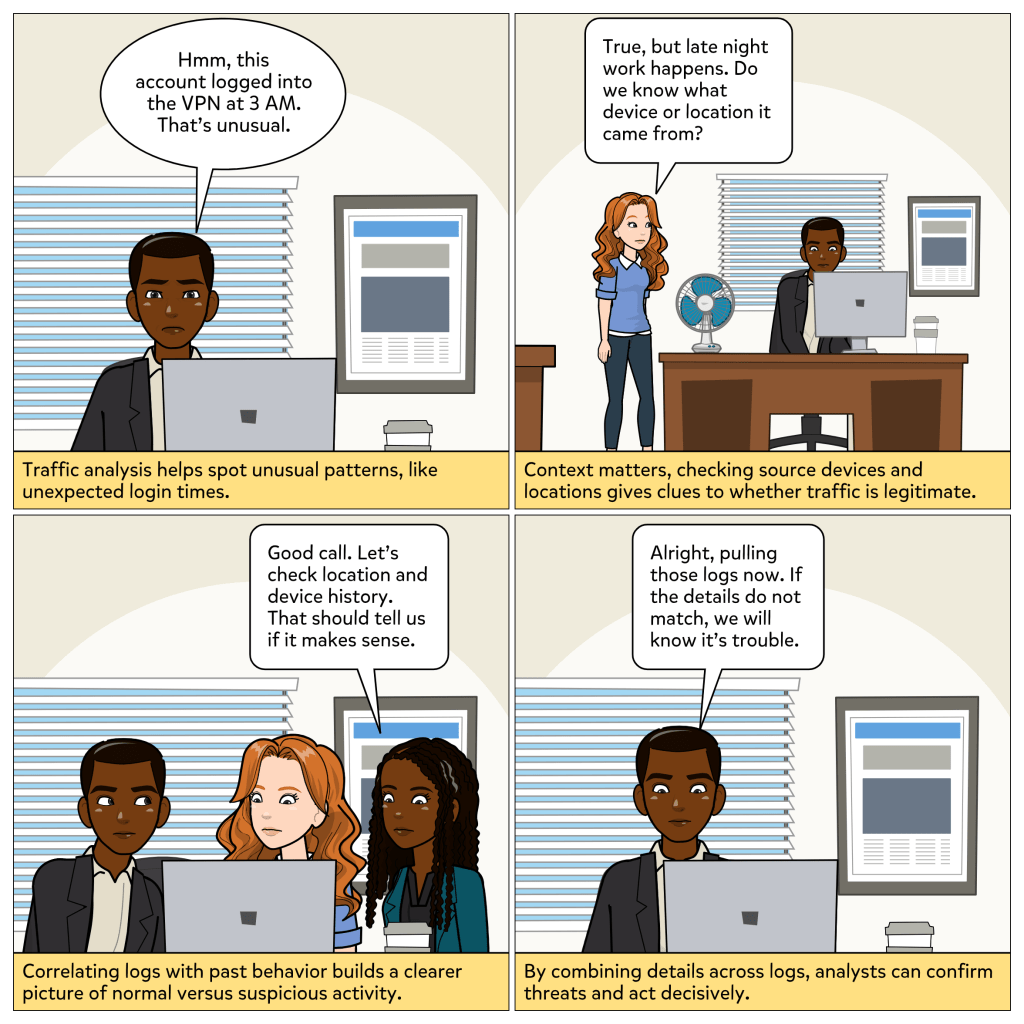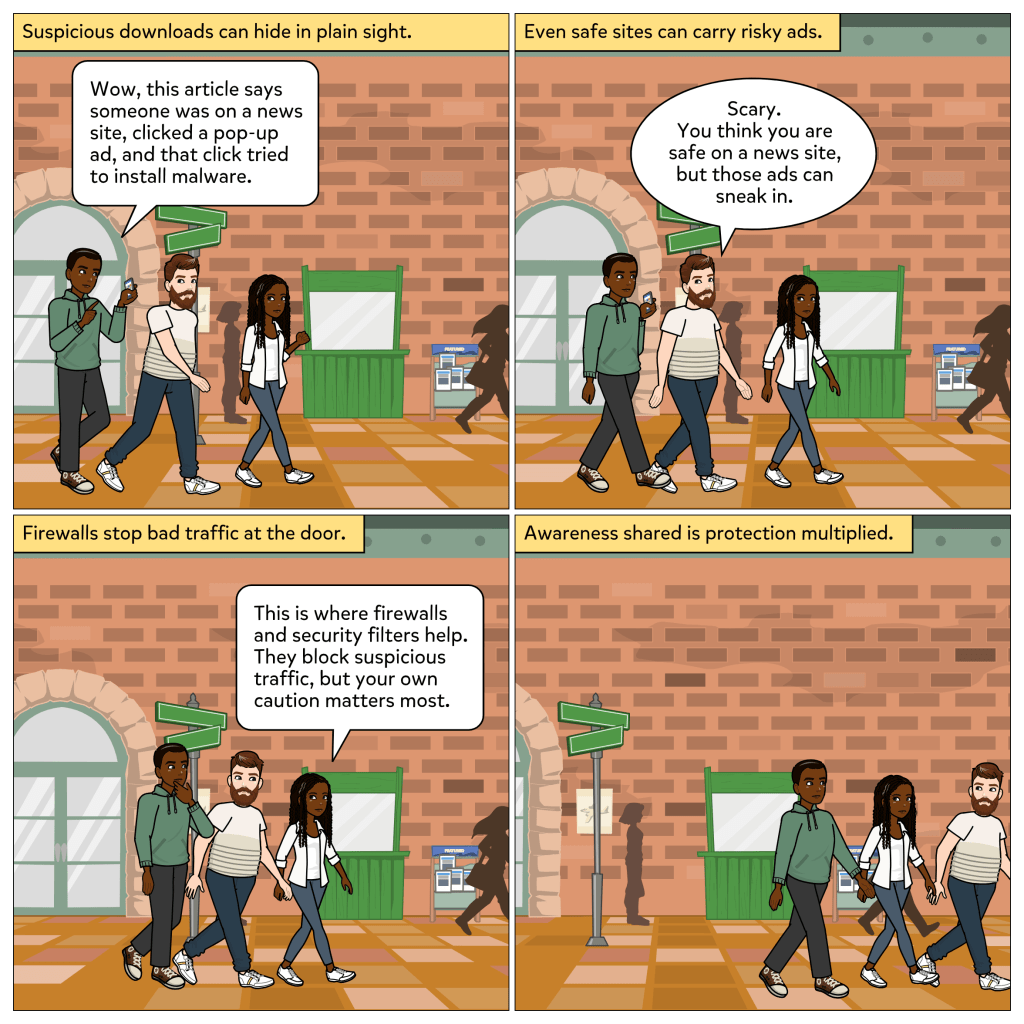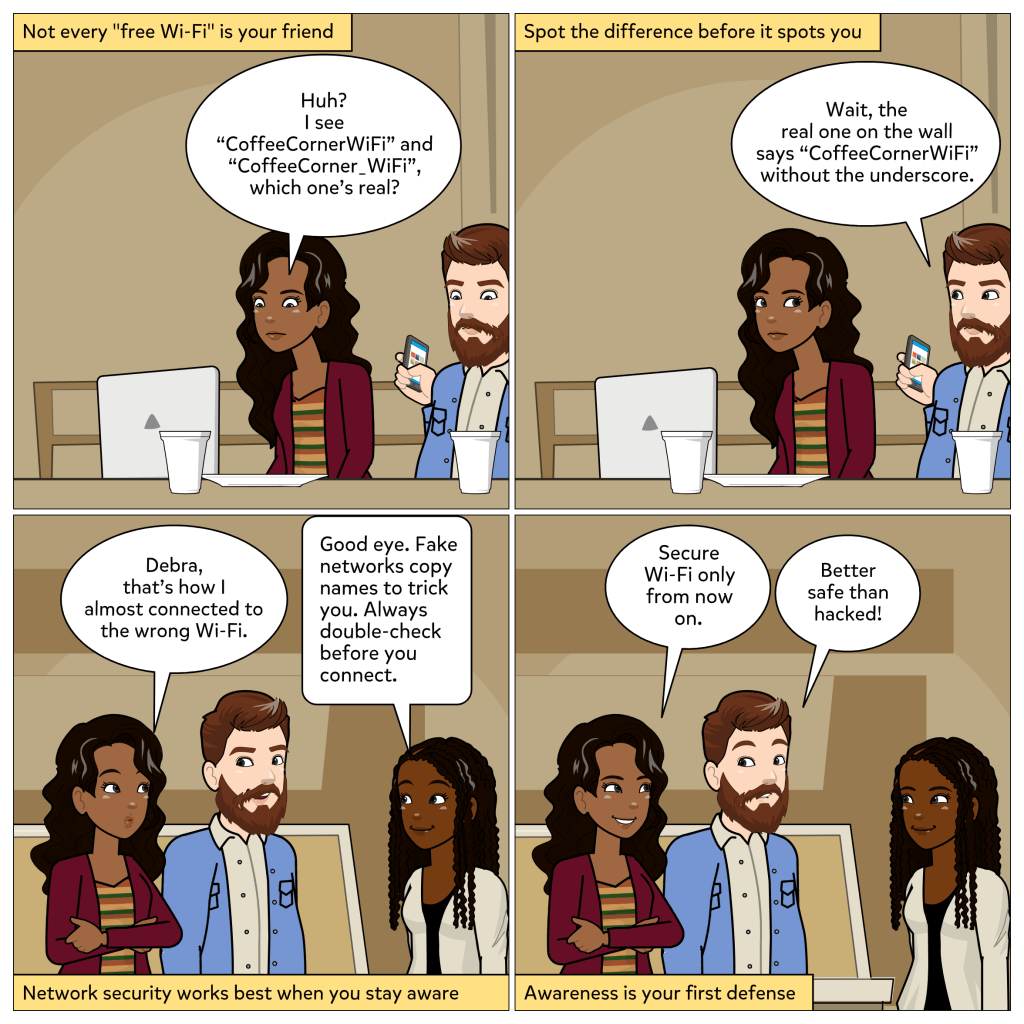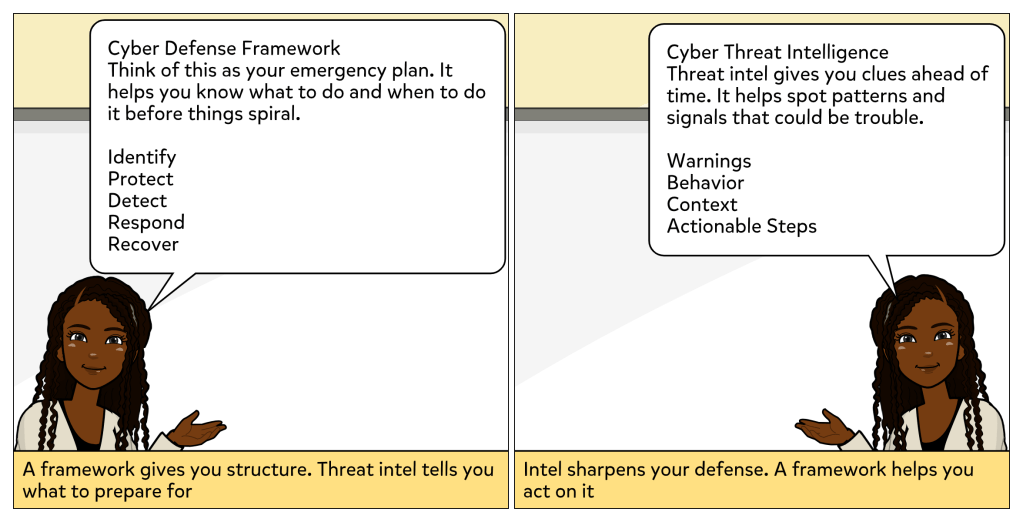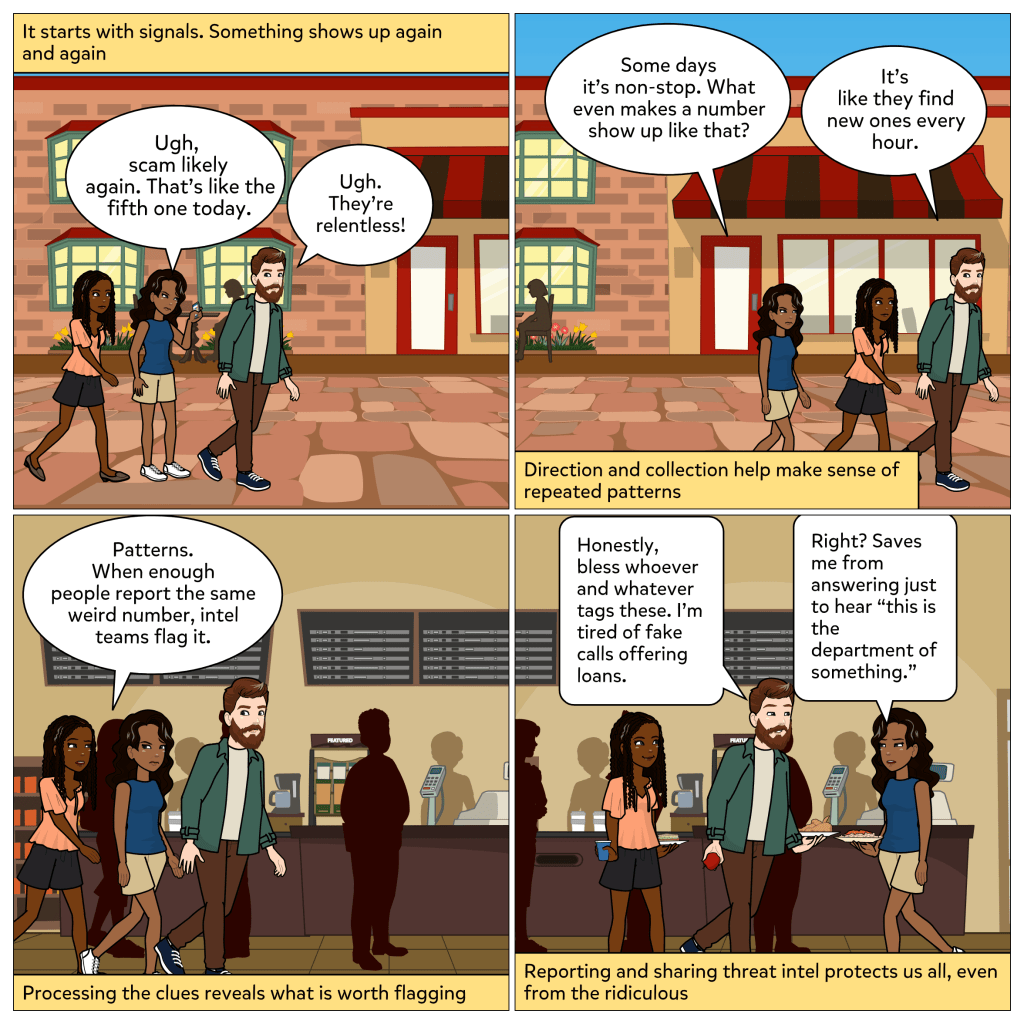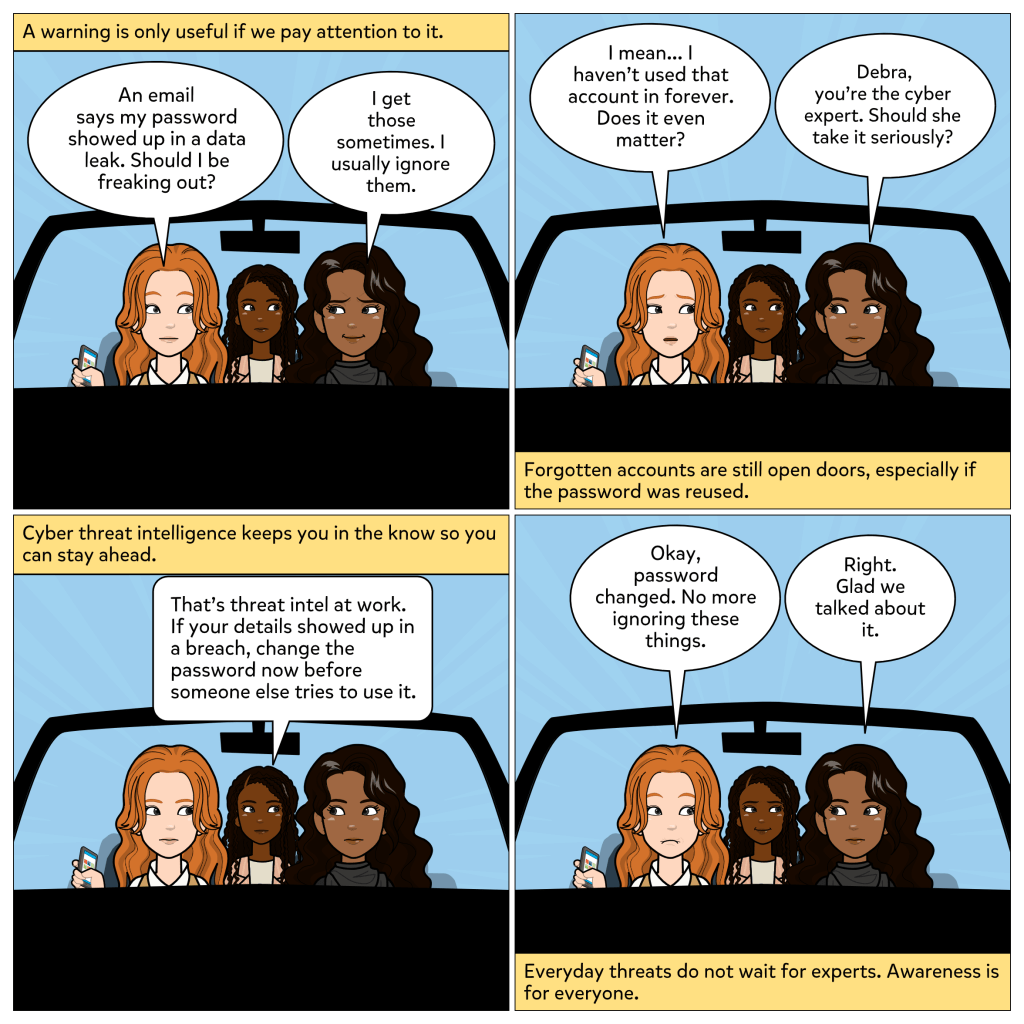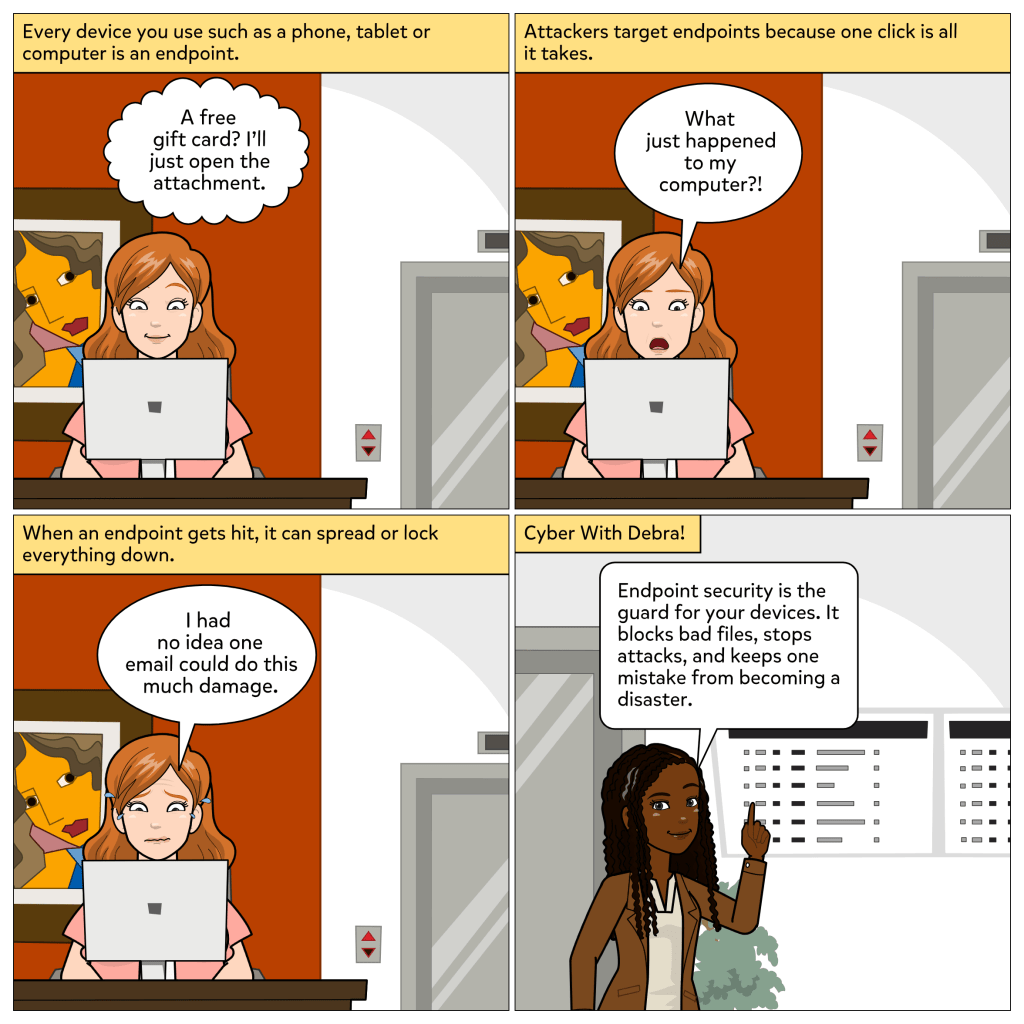
Every device you use to get work done is an endpoint, whether it is a phone, tablet, or computer. And attackers know it. If they can compromise just one, they can often move deeper into the network. That is why endpoints are such high-value targets in cybersecurity.
In this week’s comic, we see what happens when someone clicks on what looks like a harmless email attachment. At first, it seems like a free gift card is only one click away. But almost instantly, the computer locks up. That single action opens the door for an attack. The user realizes how much damage one email can cause. Then Debra steps in to explain what makes endpoint security so important: it guards your devices, blocks bad files, and prevents one mistake from becoming a disaster.
What endpoint security does
Endpoint security is not just antivirus software. It is a set of protections designed to keep the laptops, desktops, tablets, and phones we use every day from becoming the weak link. These protections can include:
• Antivirus and anti-malware to detect and stop harmful files.
• Endpoint Detection and Response (EDR) to monitor behavior, catch suspicious activity, and isolate compromised devices.
• Device controls and policies to prevent unauthorized software or risky apps from being installed.
• Regular updates and patching to close the gaps attackers often exploit.
Together, these tools and practices keep attackers from turning one device into a stepping stone for a larger breach.
Why it matters
Most cyberattacks today begin at the endpoint. People are busy, emails keep coming in, and it is easy to trust what looks familiar. Attackers count on that. They send malicious attachments or links because they know that one person clicking is often enough to get in.
Endpoint security adds an important safeguard. Even if someone makes a mistake, the system can block, detect, or contain the threat before it spreads. It is not about replacing human judgment but about making sure one slip does not compromise everything.
Everyday takeaway
Think of endpoint security like having a lock, an alarm, and a guard on every door and window in your house. If someone tries to force their way in, the protections are there to stop them or sound the alarm before real damage is done.
Endpoints are where attackers often strike first. Protecting them means protecting the whole network.
Thank you for reading. I hope you have subscribed. Let me know in the comments what stood out to you the most about endpoint security. 🖥️📱☎️ 💻